Exploit Table Contract Gratis
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.
0
Forms filled
0
Forms signed
0
Forms sent
Discover the simplicity of processing PDFs online
Upload your document in seconds

Fill out, edit, or eSign your PDF hassle-free

Download, export, or share your edited file instantly
Top-rated PDF software recognized for its ease of use, powerful features, and impeccable support






Every PDF tool you need to get documents done paper-free
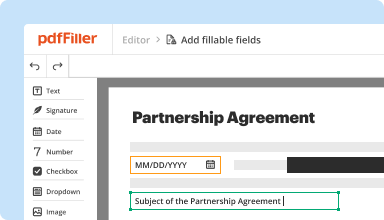
Create & edit PDFs
Generate new PDFs from scratch or transform existing documents into reusable templates. Type anywhere on a PDF, rewrite original PDF content, insert images or graphics, redact sensitive details, and highlight important information using an intuitive online editor.
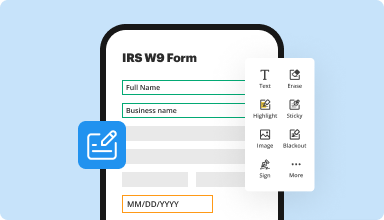
Fill out & sign PDF forms
Say goodbye to error-prone manual hassles. Complete any PDF document electronically – even while on the go. Pre-fill multiple PDFs simultaneously or extract responses from completed forms with ease.
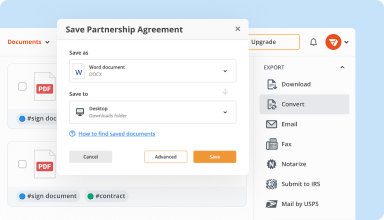
Organize & convert PDFs
Add, remove, or rearrange pages inside your PDFs in seconds. Create new documents by merging or splitting PDFs. Instantly convert edited files to various formats when you download or export them.
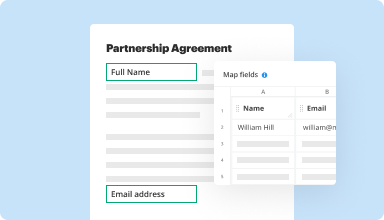
Collect data and approvals
Transform static documents into interactive fillable forms by dragging and dropping various types of fillable fields on your PDFs. Publish these forms on websites or share them via a direct link to capture data, collect signatures, and request payments.
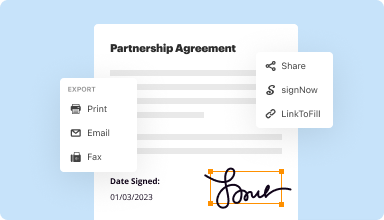
Export documents with ease
Share, email, print, fax, or download edited documents in just a few clicks. Quickly export and import documents from popular cloud storage services like Google Drive, Box, and Dropbox.
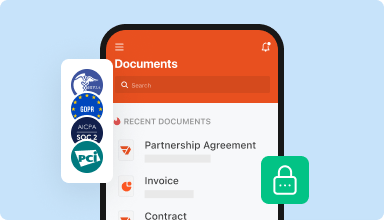
Store documents safely
Store an unlimited number of documents and templates securely in the cloud and access them from any location or device. Add an extra level of protection to documents by locking them with a password, placing them in encrypted folders, or requesting user authentication.
Customer trust by the numbers
64M+
users worldwide
4.6/5
average user rating
4M
PDFs edited per month
9 min
average to create and edit a PDF
Join 64+ million people using paperless workflows to drive productivity and cut costs
Why choose our PDF solution?
Cloud-native PDF editor
Access powerful PDF tools, as well as your documents and templates, from anywhere. No installation needed.
Top-rated for ease of use
Create, edit, and fill out PDF documents faster with an intuitive UI that only takes minutes to master.
Industry-leading customer service
Enjoy peace of mind with an award-winning customer support team always within reach.
What our customers say about pdfFiller
See for yourself by reading reviews on the most popular resources:
The service is great and the price for fax service is much less expensive than other companies. I love the fact I can fill out documents then email, fax, or file them away.
2015-02-03
chat support: wonderful spoke to 2 different people and both terrific. Love this service. I need to get forms from years back and thanks to this service they are all available in minutes.
2016-05-19
I like the program a lot. You recently changed the format a little. When I want to save a document to my computer, I can't tell it where to save it; it automatically saves it to my downloads, which I do not like. Before you changed the format, I was able to save a PDF completed document to whatever file I needed to on my computer. I would like to be able to do that again.
2017-04-15
Having great difficulty because I needed to change details on a PDF file. It was so easy once I read your instructions! Thank you so much! Is there any subscription cost for PDF filler?
2018-03-09
i liked this edit word and i aprecited,i do best sample for international student scholarship i20 form,student not needed to pay to much money agent. I did good sample sevis fee payment recipet,how they receved reciept paper for embassy good thank you
2023-12-13
This has been a very pleasant surprise as I am a avid &somewhat devoted Adobe Acrobat user &didn't think that there existed any other app that could even come anyway close in performance, features &value to what has long been the industry standard for me...They created PDF file format..but PDFfiller has made working with them much more user-friendly &intuitive. Using the two in tandem has been both very eye-Opening ,&productive!!!
2023-05-07
Great HELP
Karen was great help to me. I was looking for a file for 2 years. With her help I was finally able to find it. She was patient and knowledgeable. Thank you Kara!!!!
2021-07-16
Great customer experience with this company. Very responsive to technical questions and billing service cared more about our satisfaction than most companies even though it wasn't to their direct bottom line advantage. Will use them again surely.
2020-06-10
Exceptional services provided! Really efficient and pleasant communication with this company; they handle everything really promptly and with no problems.
2020-06-07
Exploit Table Contract Feature
The Exploit Table Contract feature offers a streamlined approach to managing and analyzing contracts. It enables you to identify vulnerabilities and optimize your contract strategies with ease. You can enhance your business efficiency while reducing risks related to contract handling.
Key Features
User-friendly interface for easy navigation
Comprehensive vulnerability assessments
Real-time updates and alerts for contract changes
Seamless integration with existing systems
Robust reporting tools for data analysis
Potential Use Cases and Benefits
Minimize the risk of contract breaches through detailed analysis
Enhance negotiation strategies based on data-driven insights
Increase collaboration among teams with shared access to contracts
Ensure compliance with regulations in various industries
Reduce time spent on contract management tasks
By implementing the Exploit Table Contract feature, you can mitigate the complexities of contract management. It helps you find and eliminate potential weaknesses in your agreements. This way, you gain confidence in your contracts and give your business the edge it needs to succeed.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What are the different types of networks attacks?
Top 20 Most Common Types of Cybersecurity Attacks DoS and DDoS attacks. Phishing attacks. Ransomware. SQL injection attacks. Brute force attacks. Trojan horses. XSS attacks.
Can smart contracts be exploited?
Overview. A reentrancy attack exploits the vulnerability in smart contracts when a function makes an external call to another contract before updating its own state. This allows the external contract, possibly malicious, to reenter the original function and repeat certain actions, like withdrawals, using the same state
What is the most common smart contract vulnerability?
THE LIST OF SMART CONTRACT VULNERABILITIES VULNERABLE PRICE FEED. REENTRANCY. INCORRECT DEPLOY AND POST-DEPLOY SETTINGS. INFLATION ATTACK. RELATED TO STOLEN PRIVATE KEYS. ATTACK WITH CONTRACT. INCORRECT CALCULATIONS & ACCURACY LOSS. RACE CONDITION – DEPENDENCY ON THE ORDER.
What does exploit mean in a contract?
Exploitation is “one of the contracting parties taking advantage of the weakness of the other contracting party, to obtain advantages that are not matched by the benefit of this.” Hence, exploitation is the psychological manifestation of a lesion, which varies with this benefit in an unusual way.
What are the attacks of smart contracts?
The smart contract security issues with reentrancy could take the form of multiple types of attacks. Some of the common types of reentrancy attacks include single-function, read-only, cross-function, and cross-contract reentrancy attacks.
What are the different types of attacks in cryptography?
8 Types of Attack in Cryptography Brute Force. Cipher Only Attack. Known Plaintext Attack. Chosen Plaintext Attack. Chosen Ciphertext Attack. Key and Algorithm Attack. Side Channel Attacks. Replay Attacks.
What are the common Solidity attacks?
What are common Solidity security vulnerabilities? Common vulnerabilities include reentrancy attacks, integer overflow and underflow, and improper access control.
What are the different types of attacks on smart contracts?
The smart contract security issues with reentrancy could take the form of multiple types of attacks. Some of the common types of reentrancy attacks include single-function, read-only, cross-function, and cross-contract reentrancy attacks.
#1 usability according to G2
Try the PDF solution that respects your time.






