Aws Signature Grátis




Join the world’s largest companies
How to Aws Signature - video instructions
Watch the video guide to learn more about pdfFiller's online Signature feature









Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution

Unlimited document storage

Widely recognized ease of use

Reusable templates & forms library
The benefits of electronic signatures

Efficiency

Accessibility

Cost savings

Security

Legality

Sustainability
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance

SOC 2 Type II Certified

PCI DSS certification

HIPAA compliance

CCPA compliance
AWS Signature Feature
The AWS Signature feature simplifies the process of securing your API calls. By providing a robust method to authenticate and ensure the integrity of requests, you can focus on building your application with confidence.
Key Features
Potential Use Cases and Benefits
By implementing the AWS Signature feature, you address the critical need for secure and authenticated communications in your applications. This feature not only enhances your security posture but also allows you to focus on delivering value to your users without worrying about unauthorized access.
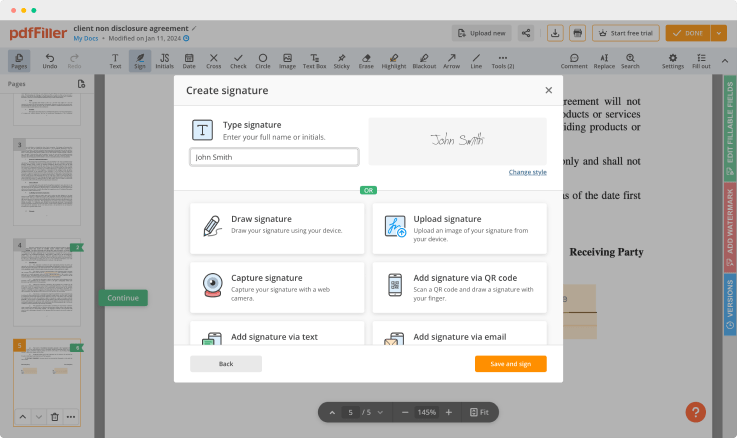
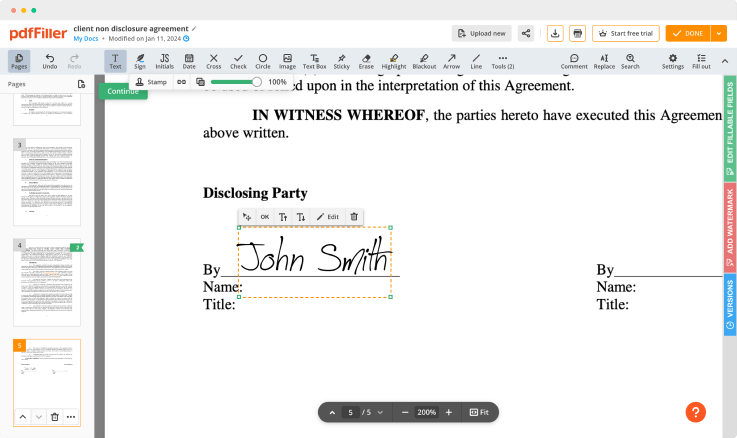
How to AWS Signature
Still using multiple applications to create and modify your documents? Use our all-in-one solution instead. Use our tool to make the process efficient. Create document templates on your own, modify existing formsand many more useful features, within your browser. You can use AWS Signature with ease; all of our features are available instantly to all users. Get an advantage over other tools.
How-to Guide
How to edit a PDF document using the pdfFiller editor:
For pdfFiller’s FAQs
Ready to try pdfFiller's? Aws Signature Grátis