Secure Year Notification Grátis
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

Upload a document

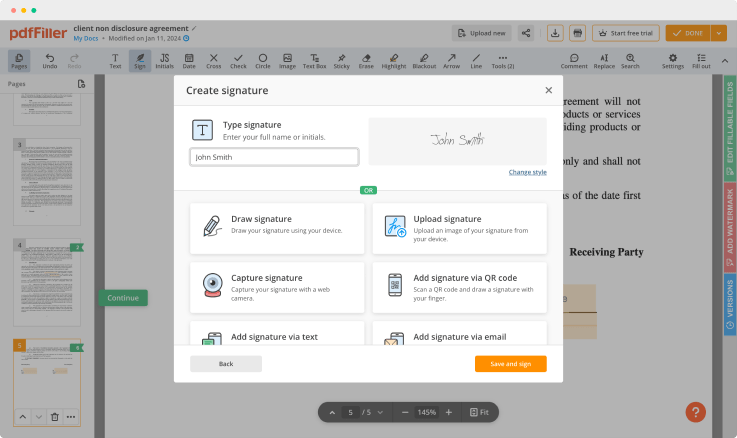
Generate your customized signature

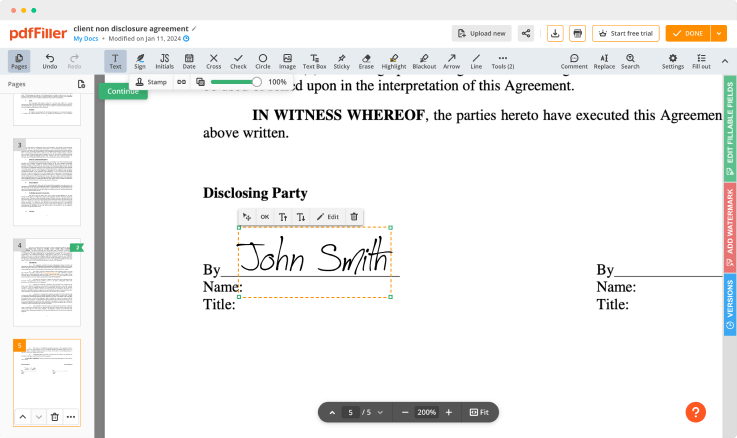
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Secure Year Notification Feature
The Secure Year Notification feature keeps you informed about critical updates and actions related to your data security. It ensures you stay connected and aware throughout the year, giving you peace of mind.
Key Features
Real-time alerts for security updates
Customizable notification preferences
Direct access to security resources
User-friendly interface
Integration with existing security tools
Potential Use Cases and Benefits
Stay updated on security threats
Be informed about important policy changes
Receive timely reminders for security checks
Manage security settings easily
Enhance overall data protection
By using the Secure Year Notification feature, you can tackle the challenge of keeping track of various security updates. It helps you reduce the risk of missing crucial information, allowing you to act promptly and secure your data effectively.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
How do I report a security breach?
Internal Revenue Service — Report client data theft to your local IRS Stakeholder Liaison. Federal Bureau of Investigation Contact your local office. Secret Service Contact your local office (if directed). Local police File a police report on the data breach.
How do I report a data security breach?
a description of the nature of the personal data breach including, where possible: the name and contact details of the data protection officer (if your organization has one) or other contact point where more information can be obtained.
What constitutes a breach of data protection?
According to the General Data Protection Regulation, a personal data breach is 'a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data transmitted, stored or otherwise processed' (Article 4, definition 12).
Do I need to report a data breach to the ICO?
You need to consider the likelihood and severity of the risk to people's rights and freedoms, following the breach. When you've made this assessment, if it's likely there will be a risk then you must notify the ICO. If it's unlikely then you don't have to report. You do not need to report every breach to the ICO.
How do you handle a data breach?
Stop the breach. Assess the damage. Notify those affected. Security audit. Update your recovery plan to prepare for future attacks. Train your employees. Protect the data. Enforce strong passwords.
How do you respond to a security breach?
Contain/Isolate Data Loss. Quickly assess the business impact. Notify the Incident Response Team & Forensic Team. Notify legal advisory team & communication team. Guard the Incident site for forensic proof protection.
How do you respond to a data breach?
Stay calm and take the time to investigate thoroughly. Get a response plan in place before you turn the business switch back on. Notify your customers and follow your state's reporting laws. Call in your security and forensic experts to identify and fix the problem.
What happens when there is a security breach?
A security breach occurs when an intruder gains unauthorised access to an organisation's protected systems and data. Cybercriminals or malicious applications bypass security mechanisms to reach restricted areas. A security breach is an early-stage violation that can lead to things like system damage and data loss.
Ready to try pdfFiller's? Secure Year Notification Grátis
Upload a document and create your digital autograph now.