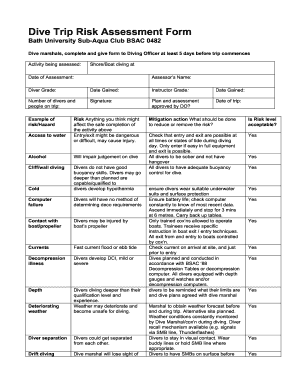
Information Security Risk Assessment Example
What is information security risk assessment example?
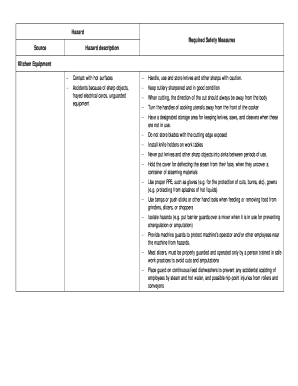
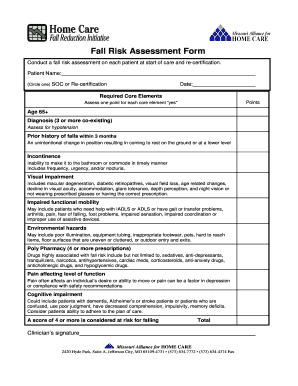
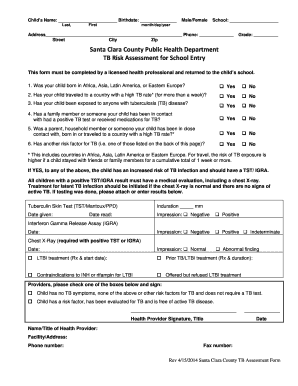
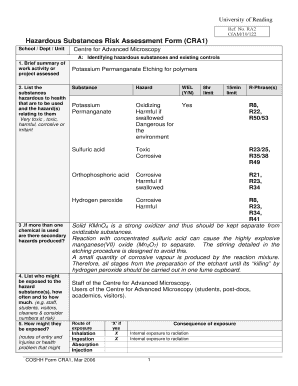
Information security risk assessment is the process of identifying, evaluating, and mitigating potential risks to the security of an organization's information. It involves analyzing the possible threats, vulnerabilities, and impacts on the confidentiality, integrity, and availability of information. For example, an information security risk assessment could involve assessing the risk of a data breach, system outage, or unauthorized access to sensitive information.
What are the types of information security risk assessment example?
There are several types of information security risk assessment examples that organizations can use to assess their information security risks. Some of the commonly used types include:
How to complete information security risk assessment example
Completing an information security risk assessment example involves several steps. Here is a step-by-step guide to help you complete the assessment:
pdfFiller empowers users to create, edit, and share documents online, offering unlimited fillable templates and powerful editing tools. With pdfFiller, users have everything they need to efficiently complete their documents and ensure security. Try pdfFiller today!