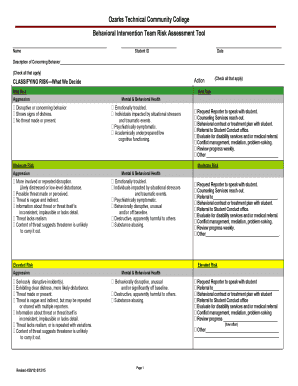
What is threat and risk assessment working guide?
A threat and risk assessment working guide is a comprehensive document that outlines the steps and processes involved in assessing and managing threats and risks in a particular context. It provides a structured approach to identify potential threats, evaluate the associated risks, and develop strategies to mitigate or eliminate them. The guide serves as a valuable resource for individuals and organizations to proactively address potential threats and make informed decisions to safeguard their interests.
What are the types of threat and risk assessment working guide?
There are various types of threat and risk assessment working guides, each tailored to specific industries or domains. Some common types include:
Financial risk assessment guide: focuses on identifying and mitigating financial risks that may impact an organization's financial stability and performance.
Cybersecurity risk assessment guide: helps assess and address risks associated with data breaches, cyber-attacks, and information security.
Physical security risk assessment guide: guides the evaluation and management of physical risks such as theft, vandalism, or unauthorized access to premises.
Operational risk assessment guide: assesses risks related to day-to-day operations, including process failures, supply chain disruptions, or equipment malfunction.
Environmental risk assessment guide: focuses on identifying and mitigating potential environmental hazards and risks, such as pollution or natural disasters.
Health and safety risk assessment guide: helps identify and mitigate workplace health and safety risks to ensure the well-being of employees and compliance with regulations.
How to complete threat and risk assessment working guide
Completing a threat and risk assessment working guide requires a systematic approach and attention to detail. Here are the steps to follow:
01
Identify the potential threats: Brainstorm and research the potential threats specific to your industry, location, or organization.
02
Evaluate the risks: Assess the likelihood and potential impact of each threat on your organization.
03
Develop risk mitigation strategies: Determine effective strategies to mitigate or eliminate the identified risks.
04
Implement risk mitigation measures: Put the identified strategies into action by implementing necessary changes or controls.
05
Monitor and review: Continuously monitor the effectiveness of risk mitigation measures and review the assessment regularly to account for changes or emerging threats.
06
Update the guide: Keep the threat and risk assessment working guide up-to-date with the latest information, practices, and lessons learned.
pdfFiller empowers users to create, edit, and share documents online. Offering unlimited fillable templates and powerful editing tools, pdfFiller is the only PDF editor users need to get their documents done.