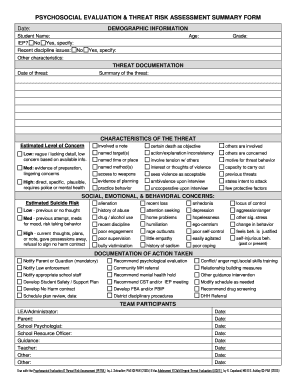
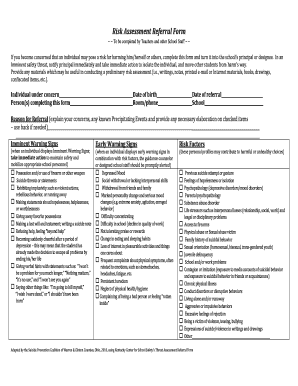
Threat Risk Assessment Checklist
What is threat risk assessment checklist?
A threat risk assessment checklist is a tool used to systematically identify and evaluate potential threats and risks to a specific entity or organization. It helps in identifying vulnerabilities, assessing their potential impact, and developing strategies to mitigate and manage those risks.
What are the types of threat risk assessment checklist?
There are several types of threat risk assessment checklists, including:
Physical threats checklist
Cybersecurity threats checklist
Operational threats checklist
Natural disasters checklist
How to complete threat risk assessment checklist
Completing a threat risk assessment checklist involves the following steps:
01
Identify potential threats and risks specific to your organization or entity.
02
Assess the likelihood and potential impact of each identified threat.
03
Evaluate existing security measures and identify any gaps or vulnerabilities.
04
Develop and implement mitigation strategies to reduce the identified risks.
05
Regularly review and update the checklist to ensure its effectiveness in managing risks.
pdfFiller empowers users to create, edit, and share documents online. Offering unlimited fillable templates and powerful editing tools, pdfFiller is the only PDF editor users need to get their documents done.
Video Tutorial How to Fill Out threat risk assessment checklist
Thousands of positive reviews can’t be wrong
Read more or give pdfFiller a try to experience the benefits for yourself
Questions & answers
How do I create a risk assessment template?
Basic Risk Assessment Template A description of the procedure, task, or worksite being assessed. Identify the hazards and document them. Identify the risks associated with each activity. Attach photos of the hazards. Determine a risk rating. Document the specific control measures taken to mitigate the risk.
What are the 5 parts of threat assessment?
Intentional Threats. Accidental Threats. Natural Disasters. Internal Threats. Determine the Scope of Your Threat Assessment. Collect Necessary Data to Cover the Full Scope of Your Threat Assessment. Identify Potential Vulnerabilities That Can Lead to Threats. Analyze Any Threats You Uncover and Assign a Rating.
How do you perform a threat risk assessment?
determine inherent risks and impacts. analyze and identify existing controls that may prevent, mitigate, detect, or compensate for potential threats. Assess the extent that existing controls successfully mitigate the threats. calculate a risk rating based on a combination of impact and likelihood of occurrence.
How do you write a simple risk assessment?
Step 1: Identify the hazards. Step 2: Decide who might be harmed and how. Step 3: Evaluate the risks and decide on precautions. Step 4: Record your findings and implement them. Step 5: Review your risk assessment and update if.
Can I create my own risk assessment?
It's important that you make risk assessments your own — copied risk assessments won't meet legal requirements. Every company will have unique hazards and risks, so risk assessments will only be relevant and effective if they're specific to your business and company operations.
How do you do a threat risk assessment?
The Cyber-security Threat and Risk Assessment analyze and identify existing controls that may prevent, mitigate, detect, or compensate for potential threats. Assess the extent that existing controls successfully mitigate the threats. calculate a risk rating based on a combination of impact and likelihood of occurrence.
Related templates