Get the free 3502 Information Security Guideline - BCIT - bcit
Show details
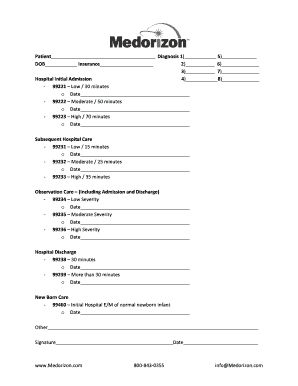
Guideline Information Security Guideline No.: Policy Reference: Category: Department Responsible: Current Approved Date: 3502-GU1 3502 Information Management Information Technology Services 2011 May
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign
Edit your 3502 information security guideline form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your 3502 information security guideline form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing 3502 information security guideline online
To use the professional PDF editor, follow these steps:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit 3502 information security guideline. Add and replace text, insert new objects, rearrange pages, add watermarks and page numbers, and more. Click Done when you are finished editing and go to the Documents tab to merge, split, lock or unlock the file.
4
Save your file. Choose it from the list of records. Then, shift the pointer to the right toolbar and select one of the several exporting methods: save it in multiple formats, download it as a PDF, email it, or save it to the cloud.
It's easier to work with documents with pdfFiller than you could have ever thought. You can sign up for an account to see for yourself.
How to fill out 3502 information security guideline
01
Start by reviewing the purpose and scope of the 3502 information security guideline. Understand the specific requirements and objectives outlined in the document.
02
Familiarize yourself with the current information security practices and policies within your organization. This will help you align your responses with the existing security framework.
03
Begin filling out the guideline by providing accurate and up-to-date information about your organization. Include details such as the company name, address, and contact information.
04
Identify the personnel responsible for managing information security within your organization. This may include IT managers, security officers, or designated individuals responsible for policy implementation.
05
Provide information about the assets and resources that need to be protected. This can include data, systems, networks, and physical infrastructure. Be specific about the types of information involved (e.g., customer data, financial records).
06
Document any existing security controls or measures that are already in place. This can include firewalls, encryption methods, access controls, or employee training programs. Emphasize how these measures align with the guideline's requirements.
07
Assess the potential risks and vulnerabilities your organization may face. This can include cybersecurity threats, physical breaches, or human error. Consider any past incidents or breaches that have occurred.
08
Detail the procedures and policies for incident response and management. This should include steps to detect, respond to, and mitigate security incidents. Include any reporting mechanisms or escalation procedures.
09
Identify any regulatory or legal requirements that impact your organization's information security practices. This can include compliance with industry-specific standards (e.g., PCI DSS, HIPAA) or data protection regulations (e.g., GDPR).
10
Finally, review and ensure that all information provided is accurate and complete. Check for any inconsistencies or gaps in the guideline and make necessary updates.
Who needs 3502 information security guideline?
01
Organizations across various industries that handle sensitive information need the 3502 information security guideline.
02
This guideline is particularly relevant for organizations in sectors such as healthcare, finance, technology, and government, where the protection of sensitive data is critical.
03
Compliance officers, IT managers, security officers, and other personnel responsible for ensuring information security within an organization would benefit from the 3502 guideline.
Fill form : Try Risk Free
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is 3502 information security guideline?
The 3502 information security guideline is a set of rules and recommendations that provide guidance on how to establish and maintain information security measures within an organization.
Who is required to file 3502 information security guideline?
The 3502 information security guideline is typically required to be filed by organizations that handle sensitive and confidential information, such as government agencies, financial institutions, and healthcare providers.
How to fill out 3502 information security guideline?
Filling out the 3502 information security guideline involves assessing the organization's information security controls, documenting the existing measures, identifying any gaps or vulnerabilities, and implementing necessary improvements. The guideline may require the completion of specific forms or documentation, which can vary depending on the organization.
What is the purpose of 3502 information security guideline?
The purpose of the 3502 information security guideline is to ensure the confidentiality, integrity, and availability of information within an organization. It aims to protect sensitive data from unauthorized access, disclosure, alteration, and destruction.
What information must be reported on 3502 information security guideline?
The specific information that must be reported on the 3502 information security guideline can vary depending on the regulatory requirements applicable to the organization. However, common elements may include risk assessments, security policies and procedures, incident response plans, security awareness training, and evidence of compliance with security standards.
When is the deadline to file 3502 information security guideline in 2023?
The deadline to file the 3502 information security guideline in 2023 may vary depending on the jurisdiction and regulatory bodies involved. It is recommended to consult the applicable regulations or authorities to determine the specific deadline.
What is the penalty for the late filing of 3502 information security guideline?
The penalty for the late filing of the 3502 information security guideline can also vary depending on the jurisdiction and applicable regulations. Penalties may include fines, penalties, loss of certification or accreditation, reputational damage, or other legal consequences. It is important to comply with the filing deadlines to avoid potential penalties.
Can I create an electronic signature for signing my 3502 information security guideline in Gmail?
Use pdfFiller's Gmail add-on to upload, type, or draw a signature. Your 3502 information security guideline and other papers may be signed using pdfFiller. Register for a free account to preserve signed papers and signatures.
How can I edit 3502 information security guideline on a smartphone?
Using pdfFiller's mobile-native applications for iOS and Android is the simplest method to edit documents on a mobile device. You may get them from the Apple App Store and Google Play, respectively. More information on the apps may be found here. Install the program and log in to begin editing 3502 information security guideline.
How do I fill out the 3502 information security guideline form on my smartphone?
The pdfFiller mobile app makes it simple to design and fill out legal paperwork. Complete and sign 3502 information security guideline and other papers using the app. Visit pdfFiller's website to learn more about the PDF editor's features.
Fill out your 3502 information security guideline online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Not the form you were looking for?
Keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.