Exploit Table Notice Kostenlos
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.
0
Forms filled
0
Forms signed
0
Forms sent
Discover the simplicity of processing PDFs online
Upload your document in seconds

Fill out, edit, or eSign your PDF hassle-free

Download, export, or share your edited file instantly
Top-rated PDF software recognized for its ease of use, powerful features, and impeccable support






Every PDF tool you need to get documents done paper-free
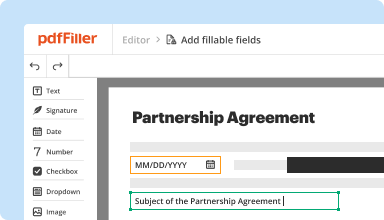
Create & edit PDFs
Generate new PDFs from scratch or transform existing documents into reusable templates. Type anywhere on a PDF, rewrite original PDF content, insert images or graphics, redact sensitive details, and highlight important information using an intuitive online editor.
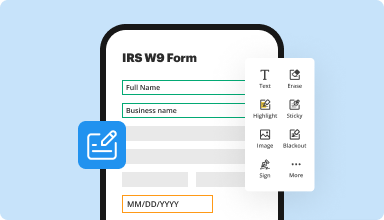
Fill out & sign PDF forms
Say goodbye to error-prone manual hassles. Complete any PDF document electronically – even while on the go. Pre-fill multiple PDFs simultaneously or extract responses from completed forms with ease.
Organize & convert PDFs
Add, remove, or rearrange pages inside your PDFs in seconds. Create new documents by merging or splitting PDFs. Instantly convert edited files to various formats when you download or export them.
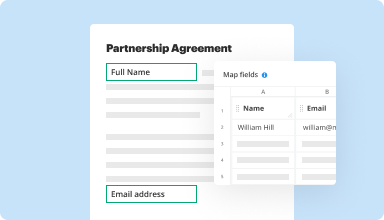
Collect data and approvals
Transform static documents into interactive fillable forms by dragging and dropping various types of fillable fields on your PDFs. Publish these forms on websites or share them via a direct link to capture data, collect signatures, and request payments.
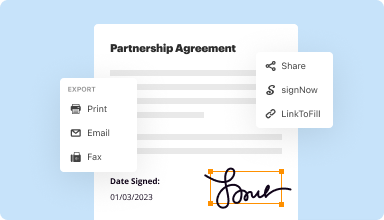
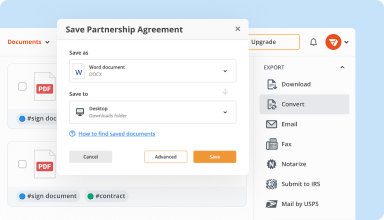
Export documents with ease
Share, email, print, fax, or download edited documents in just a few clicks. Quickly export and import documents from popular cloud storage services like Google Drive, Box, and Dropbox.
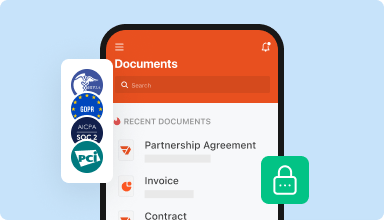
Store documents safely
Store an unlimited number of documents and templates securely in the cloud and access them from any location or device. Add an extra level of protection to documents by locking them with a password, placing them in encrypted folders, or requesting user authentication.
Customer trust by the numbers
64M+
users worldwide
4.6/5
average user rating
4M
PDFs edited per month
9 min
average to create and edit a PDF
Join 64+ million people using paperless workflows to drive productivity and cut costs
Why choose our PDF solution?
Cloud-native PDF editor
Access powerful PDF tools, as well as your documents and templates, from anywhere. No installation needed.
Top-rated for ease of use
Create, edit, and fill out PDF documents faster with an intuitive UI that only takes minutes to master.
Industry-leading customer service
Enjoy peace of mind with an award-winning customer support team always within reach.
What our customers say about pdfFiller
See for yourself by reading reviews on the most popular resources:
The forms are good but they would be much better if the user could "snap to" the proper location when typing into a box. Without a "snap to" type guide it is difficult to place the cursor in the correct location within a box and especially difficult to get columns to line up.
2014-07-08
My life has gotten so much easier since I purchased this program. My paperwork is legible and so neat when filling forms that do not have enough space.
2015-10-09
I like that my information is saved and I do not have to keep writing over my applications. I can get it quickly when I see a job I want to apply for.
2015-10-13
Naming of documents is not useful when trying to locate them at a later time. I have numerous Acord 25 forms for different entities and have to open each one to find the one I need.
2018-09-25
PDF Filler
This is a very useful program to me in my work. I can easily send documents to be filled in by customers, easy to use and easy to navigate.
I do not have any cons with this program, if you are not utilizing this you should be. It is highly useful and functional
2018-03-21
This is the best PDF program Ive used
This is the best PDF program Ive used. Ive long wanted something to compete with Adobe and this is it. I love the ease of using all features, especially the editing/adding text option. This program is top tier! As a healthcare provider who has to often complete forms for patients, this program exceeds my expectations.
2024-11-08
I find PDFFILLER to be a very a helpful and resourceful tool for all my business tax filling and contractual needs… thank you very much for this dependable tool
2021-12-13
The filler was not completing all of…
The filler was not completing all of the number I was trying to type on Florida's RT-6 for example Box 2 & 3 1,600.00 would come out 1,60 .00 Boxes 12a for the employee instead of 4,000.00 would come out 4,1 .00 With Shannen's help I got a work around. The program needs to be fixed.
2020-10-28
I needed to use the service for an application
I needed to use the service for an application! It was only needed once. The day I was going to cancel it due to no longer needing the service the money had already come out of my account. They immediately refunded it and even offered a discount if I wanted to continue using it. I highly recommend it was an easy to use service with many benefits packed in.
2020-10-15
Exploit Table Notice Feature
The Exploit Table Notice feature helps you monitor and manage vulnerabilities in your applications effectively. This tool provides essential insights that allow you to act swiftly and maintain security. With its user-friendly interface and clear notifications, you can keep your systems secure without unnecessary complications.
Key Features
Real-time notifications for detected vulnerabilities
User-friendly dashboard for easy management
Historical data tracking for informed decision-making
Customizable alerts to suit your specific needs
Integration with existing security systems
Potential Use Cases and Benefits
Monitor application vulnerabilities in real time
Ensure compliance with security regulations
Reduce downtime by addressing issues swiftly
Improve team communication through shared insights
Enhance overall security posture of your organization
By implementing the Exploit Table Notice feature, you can actively safeguard your systems against vulnerabilities. You will receive timely alerts, enabling you to take appropriate action before issues escalate. This proactive approach minimizes risks and maximizes the security of your applications.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
How is SQL injection exploited?
In SQL Injection, the UNION operator is commonly used to attach a malicious SQL query to the original query intended to be run by the web application. The result of the injected query will be joined with the result of the original query. This allows the attacker to obtain column values from other tables.
Is SQL injection still possible?
Regarding the opening questions: Yes, SQL injections are still one of the most exploited security vulnerabilities and, therefore, still a thing. In order to prevent SQL injections, there are two security testing approaches SAST and DAST. Both methods come with several limitations.
Is SQL injection still an issue?
Even though this vulnerability is known for over 20 years, injections still rank number 3 in the OWASP's Top 10 for web vulnerabilities. In 2022, 1162 vulnerabilities with the type “SQL injections” have been accepted as a CVE. So the answer is: Yes, SQL injections are still a thing.
Is SQL injection possible?
SQL Injection is a code injection technique that hackers can use to insert malicious SQL statements into input fields for execution by the underlying SQL database. This technique is made possible because of improper coding of vulnerable web applications.
How common are SQL injection attacks?
SQL Injection is the main source of web application critical vulnerabilities found globally in 2023, with 23 percent, in addition to 19 percent of internet facing critical vulnerabilities due to cross site scripting (stored) attacks.
Are SQL injections illegal?
Is SQL injection illegal? For the most part, SQL injection is illegal, although this depends on jurisdictional boundaries.
Is SQL injection still a thing in 2024?
SQL injection is still a big problem in early 2024 for developers to review and fix SQL injection vulnerabilities in their code. Having stressed the importance of SQL injection vulnerabilities, let us look at how these vulnerabilities can be exploited in practice.
How common are SQL injections?
SQL Injection is the main source of web application critical vulnerabilities found globally in 2023, with 23 percent, in addition to 19 percent of internet facing critical vulnerabilities due to cross site scripting (stored) attacks.
#1 usability according to G2
Try the PDF solution that respects your time.






