Threat And Risk Assessment Template - Page 2
What is Threat And Risk Assessment Template?
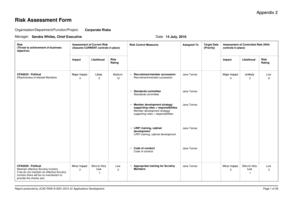
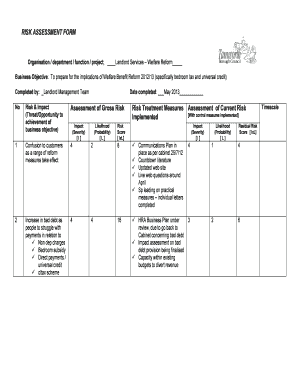
A Threat And Risk Assessment Template is a document that helps organizations identify and assess potential threats and risks to their assets, operations, and information. It provides a structured framework for evaluating the likelihood and impact of various threats and risks, allowing organizations to prioritize and implement appropriate mitigation measures.
What are the types of Threat And Risk Assessment Template?
There are several types of Threat And Risk Assessment Templates available, designed to cater to different industries and organizational needs. Some common types include:
How to complete Threat And Risk Assessment Template
Completing a Threat And Risk Assessment Template involves the following steps:
pdfFiller empowers users to create, edit, and share documents online. Offering unlimited fillable templates and powerful editing tools, pdfFiller is the only PDF editor users need to get their documents done.